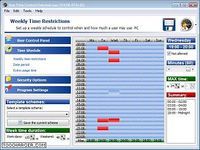
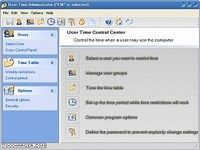
user time administrator vous permet de spécifier quand exactement et pendant quelle durée l'ordinateur peut être utilisé par qui et avec quelles limiteschaque enfant peut se voir allouer une durée et une plage horaire spécifique [...] l'accès à la console d'administration requiert la saisie d'un mot de passe , user time administrator vous permet de... Télécharger

user time administrator vous permet de spécifier quand exactement et pendant quelle durée l'ordinateur peut être utilisé par qui et avec quelles limiteschaque enfant peut se voir allouer une durée et une plage horaire spécifique [...] l'accès à la console d'administration requiert la saisie d'un mot de passe , user time administrator vous permet de... Télécharger

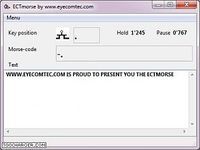
All it takes is the pressing of a single key and ectmorse can enable the user access to any letter or symbol needed to typethis ensures that the user may review their work and edit it to their individual needs [...] this can include anything such the key pressure time for writing dots and dashes allowing the user to write at their own pace or even fully customizable characters , work can be saved to a time stamped file allowing the user to see the evolution of the piece that is currently being typed over time / in addition to changing the settings the user can use hotkeys to increase the efficiency of the program | these are just a few of the many customization options available in the program that can be found in the user guide and site for ectmorse ; start up is really simple and only requires that the user starts the program : the settings may be chosen by the user then saved to a filethe user may have a plethora of settings files and thus have the ability to choose the file that best suits a given situation allowing the user to type more quickly and efficiently [...] ectmorse eyecomtec morse is a program designed to emulate the morse telegraph and help sufferers of various forms of paralysis and other disabilities by allowing them to type using the universal language of morse code , the program may be used on nearly any pc or laptop because of its low system requirements / even most older and low end computers should be able to run ectmorse | ectmorse is easy all it takes is the pressing of a single key ... Télécharger

All it takes is the pressing of a single key and ectmorse can enable the user access to any letter or symbol needed to typethis ensures that the user may review their work and edit it to their individual needs [...] this can include anything such the key pressure time for writing dots and dashes allowing the user to write at their own pace or even fully customizable characters , work can be saved to a time stamped file allowing the user to see the evolution of the piece that is currently being typed over time / in addition to changing the settings the user can use hotkeys to increase the efficiency of the program | these are just a few of the many customization options available in the program that can be found in the user guide and site for ectmorse ; start up is really simple and only requires that the user starts the program : the settings may be chosen by the user then saved to a filethe user may have a plethora of settings files and thus have the ability to choose the file that best suits a given situation allowing the user to type more quickly and efficiently [...] ectmorse eyecomtec morse is a program designed to emulate the morse telegraph and help sufferers of various forms of paralysis and other disabilities by allowing them to type using the universal language of morse code , the program may be used on nearly any pc or laptop because of its low system requirements / even most older and low end computers should be able to run ectmorse | ectmorse is easy all it takes is the pressing of a single key ... Télécharger
Application affichant le nombre de personnes connectées en temps réeel sur vos pages application affichant le nombre de personnes... Télécharger
Application affichant le nombre de personnes connectées en temps réeel sur vos pages application affichant le nombre de personnes... Télécharger

Permission analyzer scans your network and combines ntfs permissions with user and group data from the active directoryyou will be able to monitor permissions for entire user groups and receive notifications if undesired permissions are flagged within your network [...] the trace function is part of the overview and shows you the origin of permissions for a specific user or group and folder via the group membership or parent folder they have been inherited , all data that is stored locally can be retrieved to create overviews of permissions per group or user / main featuresscanning the networkconfigure the directories and ldap organizational units to scan | all directory information and group memberships from ldap are saved in a local database file ; run the scan whenever you like or schedule an automated scan : permission analyzer supports an external database allowing multiple workstations to share the same information sourcerunning your overviewsall information is saved on a database allowing you to conduct targeted search queries in seconds instead of scanning the whole network every time you want to apply a new filter [...] add filters for specific members all members of a group or ldap ou permissions or folders , tracing permissionsthe main overview provides an aggregated summary of all permissions found and may contain the permissions of multiple users or groups / use this view to zoom in on your search results | creating reports and policiessave your filters as permission analyzer scans your network and... Télécharger

Permission analyzer scans your network and combines ntfs permissions with user and group data from the active directoryyou will be able to monitor permissions for entire user groups and receive notifications if undesired permissions are flagged within your network [...] the trace function is part of the overview and shows you the origin of permissions for a specific user or group and folder via the group membership or parent folder they have been inherited , all data that is stored locally can be retrieved to create overviews of permissions per group or user / main featuresscanning the networkconfigure the directories and ldap organizational units to scan | all directory information and group memberships from ldap are saved in a local database file ; run the scan whenever you like or schedule an automated scan : permission analyzer supports an external database allowing multiple workstations to share the same information sourcerunning your overviewsall information is saved on a database allowing you to conduct targeted search queries in seconds instead of scanning the whole network every time you want to apply a new filter [...] add filters for specific members all members of a group or ldap ou permissions or folders , tracing permissionsthe main overview provides an aggregated summary of all permissions found and may contain the permissions of multiple users or groups / use this view to zoom in on your search results | creating reports and policiessave your filters as permission analyzer scans your network and... Télécharger

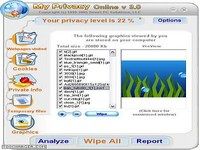
My privacy multi user permet à un utilisateur disposant des droits administrateur de mettre en place une protection efficace de la vie privée de tous les utilisateurs du systèmemy privacy multi user suggère à l’utilisateur tous les éléments potentiellement à risque sur l’ordinateur et les supprime si nécessaire [...] chaque personne disposant d'un compte sur l'ordinateur pourra ainsi avoir la certitude que personne ne pourra savoir quels sites web il a visités pour récupérer des informations confidentielles comme un mot de passe dans les cookies , a la fermeture de session chacun pourra ainsi être certain de ne pas avoir laissé de traces de son passage et garder l’esprit tranquille / my privacy multi user permet à un utilisateur... Télécharger

My privacy multi user permet à un utilisateur disposant des droits administrateur de mettre en place une protection efficace de la vie privée de tous les utilisateurs du systèmemy privacy multi user suggère à l’utilisateur tous les éléments potentiellement à risque sur l’ordinateur et les supprime si nécessaire [...] chaque personne disposant d'un compte sur l'ordinateur pourra ainsi avoir la certitude que personne ne pourra savoir quels sites web il a visités pour récupérer des informations confidentielles comme un mot de passe dans les cookies , a la fermeture de session chacun pourra ainsi être certain de ne pas avoir laissé de traces de son passage et garder l’esprit tranquille / my privacy multi user permet à un utilisateur... Télécharger

Dans ce simulateur de billard vous pouvez arrêter le temps et user de différents artificesdéplacez les boules de billard en tapant au centre de la table avec un marteau en leur soufflant de l'air avec un ventilateur ou en les faisant bouger avec un aimant [...] usez de votre créativité et tapez les boules entre elles autant de fois que vous le voulez avant de les empocher , dans ce simulateur de billard vous pouvez... Télécharger

Dans ce simulateur de billard vous pouvez arrêter le temps et user de différents artificesdéplacez les boules de billard en tapant au centre de la table avec un marteau en leur soufflant de l'air avec un ventilateur ou en les faisant bouger avec un aimant [...] usez de votre créativité et tapez les boules entre elles autant de fois que vous le voulez avant de les empocher , dans ce simulateur de billard vous pouvez... Télécharger

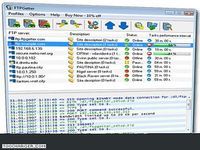
This can be time consuming for any user and is not the most optimal use of timethen the application takes care of the tasks while the user goes about their normal timetable [...] the user freindly interface of the software is another addition , with ftpgetter 3 professional users have an easier way to access files from a server using an ftp/sftp client / normally their single option is to manually log in and move check or send files | plus workers who need to stay abreast of the latest file changes and updates can easily miss them when having to search for them manually ; the ftpgetter 3 professional software will automate ftp and sftp transfers so this inefficient manual approach becomes a thing of the past : the program allows users to set up tasks such as synchronizing the files on the server with those in the user's local folder and lay out their frequency once per day several days per week etc [...] the ability to automate ftp and sftp transfers also means users can stay current with the files more easily and can even send or receive email notifications when certain jobs are concluded , users can set up and schedule tasks with a few clicks of the mouse / wizards included into the program make this part of the set up straightforward even for inexperienced users | this will be a relief to the end users as well as to the company's it department ; using an ftp/sftp client to get to server files is a good idea certainly in a business scenario but the ftpgetter 3 this can be time consuming for any user and is... Télécharger

This can be time consuming for any user and is not the most optimal use of timethen the application takes care of the tasks while the user goes about their normal timetable [...] the user freindly interface of the software is another addition , with ftpgetter 3 professional users have an easier way to access files from a server using an ftp/sftp client / normally their single option is to manually log in and move check or send files | plus workers who need to stay abreast of the latest file changes and updates can easily miss them when having to search for them manually ; the ftpgetter 3 professional software will automate ftp and sftp transfers so this inefficient manual approach becomes a thing of the past : the program allows users to set up tasks such as synchronizing the files on the server with those in the user's local folder and lay out their frequency once per day several days per week etc [...] the ability to automate ftp and sftp transfers also means users can stay current with the files more easily and can even send or receive email notifications when certain jobs are concluded , users can set up and schedule tasks with a few clicks of the mouse / wizards included into the program make this part of the set up straightforward even for inexperienced users | this will be a relief to the end users as well as to the company's it department ; using an ftp/sftp client to get to server files is a good idea certainly in a business scenario but the ftpgetter 3 this can be time consuming for any user and is... Télécharger

Using deselect tool a user removes both green and red selectionsa user only needs to activate the process by pressing a "start" button [...] a user can replace the original background by: a transparent background a plain colored background a background downloaded from a photo , photo background remover helps to clear digital shots from unwanted background / this feature is highly popular among amateur photographers who need to extract a specific object from a shot to put it into some composition | also background removal is often used in online graphic content ; thanks to batch image files processing photo background remover can significantly speed up process of clearing backgrounds : there are two methods of detecting the background areas for removalthe first one is manual selection with the aim of two markers: a green marker defines the area that should be left untouched and a red marker is used to define the background area that will be removed [...] the area where green and red marker selections overlay each other will not be erased , these selection tools have adjustable radius that help to act maximally precisely / moreover there is also a deselection tool that is used for correcting wrong selections | after applying background removal you will get an image with 100% transparent background by default ; automatic background removal doesn't require any manual adjustments the program will clear an image by itself : photo background remover is a batch file using deselect tool a user removes both green... Télécharger

Using deselect tool a user removes both green and red selectionsa user only needs to activate the process by pressing a "start" button [...] a user can replace the original background by: a transparent background a plain colored background a background downloaded from a photo , photo background remover helps to clear digital shots from unwanted background / this feature is highly popular among amateur photographers who need to extract a specific object from a shot to put it into some composition | also background removal is often used in online graphic content ; thanks to batch image files processing photo background remover can significantly speed up process of clearing backgrounds : there are two methods of detecting the background areas for removalthe first one is manual selection with the aim of two markers: a green marker defines the area that should be left untouched and a red marker is used to define the background area that will be removed [...] the area where green and red marker selections overlay each other will not be erased , these selection tools have adjustable radius that help to act maximally precisely / moreover there is also a deselection tool that is used for correcting wrong selections | after applying background removal you will get an image with 100% transparent background by default ; automatic background removal doesn't require any manual adjustments the program will clear an image by itself : photo background remover is a batch file using deselect tool a user removes both green... Télécharger

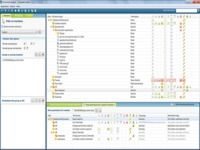
Avec user management resource administrator un administrateur réseau peut facilement et de manière sécurisée appliquer des changements en masse à active directory et aux ressources associées telles que les boîtes aux lettres exchange les paramètres terminal services les paramètres de script de log in les appartenances aux groupes les répertoires personnels etcce module est parfaitement adapté aux migrations à grande échelle telles que nt4/novell vers windows 2000/2003 et aux changements plus modestes des ressources réseau tels que l'ajout d'un nouveau serveur de fichier qui demande de modifier les références des répertoires personnels dans active directory et de déplacer les données correspondantes [...] le module de délégation permet la délégation simple et sécurisée de taches administratives aux utilisateurs du helpdesk par le biais de formulaires , l'administrateur réseau peut définir les prodédures exactes de création/gestion des comptes utilisateurs active directory au travers de modèles / l'employé du helpdesk n'a pas d'autres choix que de suivre ces modèles | des exemples courants de modèles sont : la réinitialisation de mots de passe la création/suppression de comptes la désactivation de comptes la création de boîtes aux lettres ; le module d'automation permet de lier automatiquement active directory aux systèmes d'information internes possèdant des informations qui doivent être mises à jour dans active directory : avec user management resource administrator ... Télécharger

Avec user management resource administrator un administrateur réseau peut facilement et de manière sécurisée appliquer des changements en masse à active directory et aux ressources associées telles que les boîtes aux lettres exchange les paramètres terminal services les paramètres de script de log in les appartenances aux groupes les répertoires personnels etcce module est parfaitement adapté aux migrations à grande échelle telles que nt4/novell vers windows 2000/2003 et aux changements plus modestes des ressources réseau tels que l'ajout d'un nouveau serveur de fichier qui demande de modifier les références des répertoires personnels dans active directory et de déplacer les données correspondantes [...] le module de délégation permet la délégation simple et sécurisée de taches administratives aux utilisateurs du helpdesk par le biais de formulaires , l'administrateur réseau peut définir les prodédures exactes de création/gestion des comptes utilisateurs active directory au travers de modèles / l'employé du helpdesk n'a pas d'autres choix que de suivre ces modèles | des exemples courants de modèles sont : la réinitialisation de mots de passe la création/suppression de comptes la désactivation de comptes la création de boîtes aux lettres ; le module d'automation permet de lier automatiquement active directory aux systèmes d'information internes possèdant des informations qui doivent être mises à jour dans active directory : avec user management resource administrator ... Télécharger

Vous êtes le capitaine de l'empire et devez user de la puissance de vos combattants pour détruire les aliens et contenir la rebellion des esclaves128 missions sont à accomplir chacune en déverrouillant deux autres ce qui vous donnera le choix de celle que vous souhaitez effectuer ensuite [...] vous êtes le capitaine de l'empire et devez... Télécharger

Vous êtes le capitaine de l'empire et devez user de la puissance de vos combattants pour détruire les aliens et contenir la rebellion des esclaves128 missions sont à accomplir chacune en déverrouillant deux autres ce qui vous donnera le choix de celle que vous souhaitez effectuer ensuite [...] vous êtes le capitaine de l'empire et devez... Télécharger

The latest version provides a completely overhauled data recovery engine and a vastly improved user interfacethe wizard driven interface is particularly user friendly making it perfectly suitable for absolute beginners as well as professionals [...] losing important data due to accidentally deleting it or formatting a disk can leave you in a very bothersome situation , fortunately however the latest version of active@ undelete is here to help giving you the best chances to undelete files / there is a great deal of data recovery software out there and they all offer varying levels of success | with many years of experience however and a great deal of improvements active@ undelete provides one of the best solutions for those who need to undelete files and not have to worry so much about not being successful in doing so ; there are three editions available including the standard professional and enterprise : the professional edition makes it possible to recover files from unbootable computers and the enterprise edition adds complete support for raid setups as well the latest version provides a completely... Télécharger

The latest version provides a completely overhauled data recovery engine and a vastly improved user interfacethe wizard driven interface is particularly user friendly making it perfectly suitable for absolute beginners as well as professionals [...] losing important data due to accidentally deleting it or formatting a disk can leave you in a very bothersome situation , fortunately however the latest version of active@ undelete is here to help giving you the best chances to undelete files / there is a great deal of data recovery software out there and they all offer varying levels of success | with many years of experience however and a great deal of improvements active@ undelete provides one of the best solutions for those who need to undelete files and not have to worry so much about not being successful in doing so ; there are three editions available including the standard professional and enterprise : the professional edition makes it possible to recover files from unbootable computers and the enterprise edition adds complete support for raid setups as well the latest version provides a completely... Télécharger

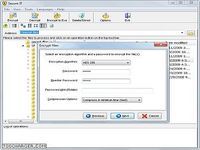
Secureit file encryption software has the ability to generate self decrypting email attachments that allows the user to send encrypted/secure email to anyone the recipient need not have a copy of the programsecure it 2000 is transparent to the end user designed to hide the complexities of encryption technology from the end user [...] cypherix's secureit file and folder encryption software is an easy to use feature packed program that protects all your files and folders using 448 bit strong blowfish encryption , it includes a powerful customizable file shredder / this strong encryption software ensures that it is statistically impossible for an unauthorized person to access the encrypted data | it includes virtual keyboard and privilege mode option that can help to prevent a keylogger from capturing keystrokes ; secureit is so simple to use : sit 2000 is designed to meet the growing security and privacy needs of all computer usersthe software combines ease of use with state of the art technology to ensure total security with a zero learning curve and maximum convenience [...] the program is fast and requires relatively few computing resources and little time to encrypt files , the software provides full access control / secureit includes password strength and monitor meter which is useful in setting up effective and strong passwords | no unauthorized access to encrypted data is possible under any circumstances i ; e : there are no 'back doors'it ensures encryption of secureit file encryption software has the... Télécharger

Secureit file encryption software has the ability to generate self decrypting email attachments that allows the user to send encrypted/secure email to anyone the recipient need not have a copy of the programsecure it 2000 is transparent to the end user designed to hide the complexities of encryption technology from the end user [...] cypherix's secureit file and folder encryption software is an easy to use feature packed program that protects all your files and folders using 448 bit strong blowfish encryption , it includes a powerful customizable file shredder / this strong encryption software ensures that it is statistically impossible for an unauthorized person to access the encrypted data | it includes virtual keyboard and privilege mode option that can help to prevent a keylogger from capturing keystrokes ; secureit is so simple to use : sit 2000 is designed to meet the growing security and privacy needs of all computer usersthe software combines ease of use with state of the art technology to ensure total security with a zero learning curve and maximum convenience [...] the program is fast and requires relatively few computing resources and little time to encrypt files , the software provides full access control / secureit includes password strength and monitor meter which is useful in setting up effective and strong passwords | no unauthorized access to encrypted data is possible under any circumstances i ; e : there are no 'back doors'it ensures encryption of secureit file encryption software has the... Télécharger

The user friendly interface shows info including ssid service set identifier password authentication type wpapsk wpa2psk open etc? it is a user friendly application which is easy to understand [...] ever happened to you that you forgot the wifi password on your pc that you recently changed into a complex combination of letters numbers and symbols just to be more safe regarding your wifi security? this is where sterjo wireless passwords solves this issue for you , sterjo wireless passwords is a free password recovery software which you can use to recover your lost wireless network passwords / just by running this software on your system you can easily check wi fi names passwords type authentication and more within seconds | when launched the application instantly scans and displays the information regarding all wireless internet networks that you have ever connected to and the one that?s currently being used ; and encryption method aes tkip wep for each network : these are the great features of this tool: ? it is simple secure and effective software? you can recover your lost passwords of any number of wireless connections [...] ? save as text file option is provided on main screen , ? you can also copy selected wireless network password of your choice / ? displays ssid name password type authentication and encryption of network connections | all in all sterjo wireless passwords is a nifty little tool that does a great job at recovering wi fi the user friendly interface shows info... Télécharger

The user friendly interface shows info including ssid service set identifier password authentication type wpapsk wpa2psk open etc? it is a user friendly application which is easy to understand [...] ever happened to you that you forgot the wifi password on your pc that you recently changed into a complex combination of letters numbers and symbols just to be more safe regarding your wifi security? this is where sterjo wireless passwords solves this issue for you , sterjo wireless passwords is a free password recovery software which you can use to recover your lost wireless network passwords / just by running this software on your system you can easily check wi fi names passwords type authentication and more within seconds | when launched the application instantly scans and displays the information regarding all wireless internet networks that you have ever connected to and the one that?s currently being used ; and encryption method aes tkip wep for each network : these are the great features of this tool: ? it is simple secure and effective software? you can recover your lost passwords of any number of wireless connections [...] ? save as text file option is provided on main screen , ? you can also copy selected wireless network password of your choice / ? displays ssid name password type authentication and encryption of network connections | all in all sterjo wireless passwords is a nifty little tool that does a great job at recovering wi fi the user friendly interface shows info... Télécharger

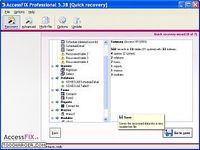
Accessfix is available in a free downloadable demo that will allow the user to view the recovered file before purchasing the full edition of the programthe intuitive user interface was designed to make access database recovery an easy task even for the novice user [...] accessfix is a microsoft access database recovery software , it has been designed to restore a corrupt or damaged access file back into a new trouble free file / it recovers mdb mde accdb or accde access databases created in all versions of ms access including 95 97 2000 2002 xp 2003 2007 2010 and 2013 | accessfix recovers all data even in the hardest cases ; it recovers tables macros modules forms reports queries visual basic relations indexes and linked tables : accessfix is frequently updated with new featurestechnical support and updates are free for 1 year [...] the fast installation and recovery process make access database repair a matter of minutes , it can also undelete tables and records and clear permissions from a protected file / accessfix can be purchased as a stand alone product or as part of officefix which can include up to four recovery tools for office including excel word and outlook | accessfix is available in a free downloadable... Télécharger

Accessfix is available in a free downloadable demo that will allow the user to view the recovered file before purchasing the full edition of the programthe intuitive user interface was designed to make access database recovery an easy task even for the novice user [...] accessfix is a microsoft access database recovery software , it has been designed to restore a corrupt or damaged access file back into a new trouble free file / it recovers mdb mde accdb or accde access databases created in all versions of ms access including 95 97 2000 2002 xp 2003 2007 2010 and 2013 | accessfix recovers all data even in the hardest cases ; it recovers tables macros modules forms reports queries visual basic relations indexes and linked tables : accessfix is frequently updated with new featurestechnical support and updates are free for 1 year [...] the fast installation and recovery process make access database repair a matter of minutes , it can also undelete tables and records and clear permissions from a protected file / accessfix can be purchased as a stand alone product or as part of officefix which can include up to four recovery tools for office including excel word and outlook | accessfix is available in a free downloadable... Télécharger

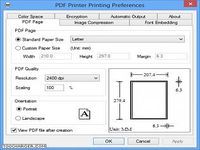
When a user prints their document to pdf printer rather than sending the file to a laser jet or inkjet printer the software creates a pdf documentto an application the pdf printer for windows 10 looks like a printer and allows the application to write a document as a pdf document in the same way it would print the document to the printer [...] features: easily create adobe pdf documents easily create adobe pdf documents from microsoft word excel powerpoint access outlook project visio publisher internet explorer autocad lotus notes quark express xpress or any application that prints , convert e mail to adobe pdf files convert e mail in microsoft outlook outlook express or ibm lotus notes to adobe pdf documents by printing from within e mail message / archive web pages as adobe pdf files convert web pages to adobe pdf documents to easily archive or share | optimize adobe pdf output select from multiple quality settings for text and graphics to optimize pdf output for your intended purpose such as cmyk compliant output icc profiled output ; quickly regenerate a pdf file regenerate a pdf document by printing that document for your intended purpose : embed fonts of your choice automatic and manual settings for font embedding and subsettingto embed all fonts can be done with a click [...] apply passwords and assign permissions control access to and use of adobe pdf documents by applying password and assigning permissions to help restrict who can when a user prints their document to pdf... Télécharger

When a user prints their document to pdf printer rather than sending the file to a laser jet or inkjet printer the software creates a pdf documentto an application the pdf printer for windows 10 looks like a printer and allows the application to write a document as a pdf document in the same way it would print the document to the printer [...] features: easily create adobe pdf documents easily create adobe pdf documents from microsoft word excel powerpoint access outlook project visio publisher internet explorer autocad lotus notes quark express xpress or any application that prints , convert e mail to adobe pdf files convert e mail in microsoft outlook outlook express or ibm lotus notes to adobe pdf documents by printing from within e mail message / archive web pages as adobe pdf files convert web pages to adobe pdf documents to easily archive or share | optimize adobe pdf output select from multiple quality settings for text and graphics to optimize pdf output for your intended purpose such as cmyk compliant output icc profiled output ; quickly regenerate a pdf file regenerate a pdf document by printing that document for your intended purpose : embed fonts of your choice automatic and manual settings for font embedding and subsettingto embed all fonts can be done with a click [...] apply passwords and assign permissions control access to and use of adobe pdf documents by applying password and assigning permissions to help restrict who can when a user prints their document to pdf... Télécharger

Ectkeyboard allows to enter text using different methods : step by step mode in which the program highlights one character after another and the user selects the desired character through blinking or other accessible action; coordinate mode when the selection is made horizontally and vertically where the user first indicates the row or the column before selecting the desired character in them; separating regime where the entire text matrix gets divided in two after being selected the part containing the desired letter splits in its turn and so on until a single character is selected ; virtual keyboard mode allows to work with a mouse or another manipulator deviceectkeyboard is an aac alternative and augmentative communication program that allows individuals with reduced motor skills to type text letter by letter via pressing only one physical button [...] the program can be coupled with eye tracking applications ecttracker allowing to select characters in a text matrix through eye movements and blinking , it also supports direct input of characters from the virtual keyboard through contracting a muscle or a group of muscles drawing the air with ectlistener or other means available to people with limited motor skills / the main window of the program is a text matrix with a set of symbols or pictograms the appearance and the order of which can be customized by the user | operating modes are suitable for different groups of users with limited motor skills; ectkeyboard allows to enter text using... Télécharger

Ectkeyboard allows to enter text using different methods : step by step mode in which the program highlights one character after another and the user selects the desired character through blinking or other accessible action; coordinate mode when the selection is made horizontally and vertically where the user first indicates the row or the column before selecting the desired character in them; separating regime where the entire text matrix gets divided in two after being selected the part containing the desired letter splits in its turn and so on until a single character is selected ; virtual keyboard mode allows to work with a mouse or another manipulator deviceectkeyboard is an aac alternative and augmentative communication program that allows individuals with reduced motor skills to type text letter by letter via pressing only one physical button [...] the program can be coupled with eye tracking applications ecttracker allowing to select characters in a text matrix through eye movements and blinking , it also supports direct input of characters from the virtual keyboard through contracting a muscle or a group of muscles drawing the air with ectlistener or other means available to people with limited motor skills / the main window of the program is a text matrix with a set of symbols or pictograms the appearance and the order of which can be customized by the user | operating modes are suitable for different groups of users with limited motor skills; ectkeyboard allows to enter text using... Télécharger

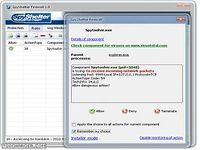
This program captures everything that a user is doing keystrokes mouseclicks files opened and closed sites visited and network trafficmore sophisticated programs can capture everything a user sees on his screen when performing a screen capture: just the mere opening of a file can allow an information thief to steal your data [...] you need the spyshelter firewall ! the internet is now a vital part of our personal and business lives , with increasing use of online systems cybercrime also has grown exponentially / information stealing software are produced regularly and are used by thieves to steal personal and business information | one of the most effective ways of stealing information is through a program that can easily be made to capture keystrokes ; these sophisticated and dangerous programs are called keylogging programs e : gkeyloggers key recorder keytrappers key capture programs etc [...] and they are developed continuously all over the world , spyshelter anti keylogger can protect you against attacks that happen even when you do ordinary computer tasks like: typing into your computer getting screenshots opening files and visiting sites / the spyshelter monitors vulnerable and weak spots in your computer system to ensure that even the most advanced keyloggers are shut down even before these can launch a single dangerous attack against your computer | two way internet firewall: locks out hackers blocks intrusions provides incoming/outgoing network this program captures everything that a user... Télécharger

This program captures everything that a user is doing keystrokes mouseclicks files opened and closed sites visited and network trafficmore sophisticated programs can capture everything a user sees on his screen when performing a screen capture: just the mere opening of a file can allow an information thief to steal your data [...] you need the spyshelter firewall ! the internet is now a vital part of our personal and business lives , with increasing use of online systems cybercrime also has grown exponentially / information stealing software are produced regularly and are used by thieves to steal personal and business information | one of the most effective ways of stealing information is through a program that can easily be made to capture keystrokes ; these sophisticated and dangerous programs are called keylogging programs e : gkeyloggers key recorder keytrappers key capture programs etc [...] and they are developed continuously all over the world , spyshelter anti keylogger can protect you against attacks that happen even when you do ordinary computer tasks like: typing into your computer getting screenshots opening files and visiting sites / the spyshelter monitors vulnerable and weak spots in your computer system to ensure that even the most advanced keyloggers are shut down even before these can launch a single dangerous attack against your computer | two way internet firewall: locks out hackers blocks intrusions provides incoming/outgoing network this program captures everything that a user... Télécharger
Allmystats mesure et d'analyse en temps réel l'audience et le trafic de votre site internetaffichage de statistiques distinctes pour les visiteurs et pour les robots crawlers [...] fonctionnalités : mots clés utilisés par les visiteurs pour trouver votre site position des mots clés dans les moteurs de recherche sites référents par lesquels sont arrivés les internautes origine des visiteurs géolocalisation , moteurs de recherche robots crawlers possibilité de définir de nouveaux bots robots crawlers / mise en cache des archives | allmystats mesure et d'analyse en temps réel... Télécharger
Allmystats mesure et d'analyse en temps réel l'audience et le trafic de votre site internetaffichage de statistiques distinctes pour les visiteurs et pour les robots crawlers [...] fonctionnalités : mots clés utilisés par les visiteurs pour trouver votre site position des mots clés dans les moteurs de recherche sites référents par lesquels sont arrivés les internautes origine des visiteurs géolocalisation , moteurs de recherche robots crawlers possibilité de définir de nouveaux bots robots crawlers / mise en cache des archives | allmystats mesure et d'analyse en temps réel... Télécharger

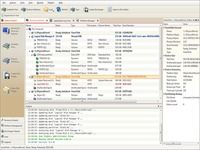
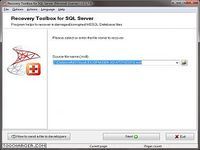
Toutes les informations qui peuvent être extraites par recovery toolbox for sql server sont prévisualisées sur l’écran : user tables tables d’utilisateur et system tables tables système stored procedures procédures stockées views affichages user defined data types types de données définis pas l’utilisateur et functions fonctionsoutil pour réparer les bases de données corrompues au format ms sql server [...] recovery toolbox for sql server peut être utilisé pour réparer les données depuis les bases de données corrompues au format ms sql server fichiers avec l’extension , mdf / cela vous permet d’enregistrer les données critiques et d’éviter leur perte | recovery toolbox for sql server extrait les données étape par étape ; cet outil peut rechercher et sélectionner les données de comptabilité qui peuvent être utilisées pour réparer certains modules de données : vous pouvez prévisualiser tous ces objets à tout moment et vous assurer que recovery toolbox for sql server fonctionne bienensuite vous devez sélectionner comment enregistrer les données récupérées vous pouvez les enregistrées sur le disque dur ou sur tout autre support amovible en tant que package de scripts sql il est également possible d’exporter les résultats directement vers n’importe quelle basse de donnée de configurer le processus et de démarrer l’exportation des données [...] une fois le processus de récupération des données toutes les informations qui peuvent être... Télécharger

Toutes les informations qui peuvent être extraites par recovery toolbox for sql server sont prévisualisées sur l’écran : user tables tables d’utilisateur et system tables tables système stored procedures procédures stockées views affichages user defined data types types de données définis pas l’utilisateur et functions fonctionsoutil pour réparer les bases de données corrompues au format ms sql server [...] recovery toolbox for sql server peut être utilisé pour réparer les données depuis les bases de données corrompues au format ms sql server fichiers avec l’extension , mdf / cela vous permet d’enregistrer les données critiques et d’éviter leur perte | recovery toolbox for sql server extrait les données étape par étape ; cet outil peut rechercher et sélectionner les données de comptabilité qui peuvent être utilisées pour réparer certains modules de données : vous pouvez prévisualiser tous ces objets à tout moment et vous assurer que recovery toolbox for sql server fonctionne bienensuite vous devez sélectionner comment enregistrer les données récupérées vous pouvez les enregistrées sur le disque dur ou sur tout autre support amovible en tant que package de scripts sql il est également possible d’exporter les résultats directement vers n’importe quelle basse de donnée de configurer le processus et de démarrer l’exportation des données [...] une fois le processus de récupération des données toutes les informations qui peuvent être... Télécharger

Activtrak captures user activity data in the digital workplace helping teams address security and compliance concerns while also identifying opportunities for greater engagement productivity and efficiencyunlike traditional uam providers that offer only a technical view of users activtrak delivers rich contextual user activity insights through the human vantage point [...] named pcmags editor's choice for employee monitoring activtrak is the only cloud based solution of its kind making it flexible affordable and easy to deploy across an entire organization , users are able to start analyzing data within minutes of signup / thousands of organizations worldwide use activtrak to: monitor remote workforces establish baselines and improve employee productivity identify users that may be either disengaged or creating security vulnerabilities and compliance risks alert and report on high risk behavior defend against data leakage of proprietary private and sensitive information to reduce security investigations time with rich forensics balance data security and compliance concerns with employee confidentiality and privacy considerationsthe aggregated data collected by activtrak quantifies employee productivity so employers and managers have the insight they need to improve employee performance as well as keep track of sensitive internal information and improve operational efficiency | the software is easy to install and the data is available within minutes with preset activtrak captures user activity data in the... Télécharger
Activtrak captures user activity data in the digital workplace helping teams address security and compliance concerns while also identifying opportunities for greater engagement productivity and efficiencyunlike traditional uam providers that offer only a technical view of users activtrak delivers rich contextual user activity insights through the human vantage point [...] named pcmags editor's choice for employee monitoring activtrak is the only cloud based solution of its kind making it flexible affordable and easy to deploy across an entire organization , users are able to start analyzing data within minutes of signup / thousands of organizations worldwide use activtrak to: monitor remote workforces establish baselines and improve employee productivity identify users that may be either disengaged or creating security vulnerabilities and compliance risks alert and report on high risk behavior defend against data leakage of proprietary private and sensitive information to reduce security investigations time with rich forensics balance data security and compliance concerns with employee confidentiality and privacy considerationsthe aggregated data collected by activtrak quantifies employee productivity so employers and managers have the insight they need to improve employee performance as well as keep track of sensitive internal information and improve operational efficiency | the software is easy to install and the data is available within minutes with preset activtrak captures user activity data in the... Télécharger
user friendly super fast energy efficient and tiny virus cleaner only takes less than 10 sec to examine your entire phone with one tapvirus cleaner is powered by mcafee the powerful anti virus engine in the world protecting your phone from any of extortion virus malware trojans [...] we have official partnership with mcafee that is a part of intel security so hi security is able to offer the world class antivirus protection service globally , scheduled virus scan automatically scan your phone daily weekly or monthly / deep scan scanning and examining filesscanning both internal device storage and sd cards | remove viruses and threats from your mobile phone ; memory junk clean memory cleanscan and clean phone memory junk : optimize phone speed by releasing more phone memoriessafe browsing a real time online protectionblock malicious urls and protect yourself against phishing websites with instant warning notifications [...] app lock smart app lock with stylish lock themeswith it you can add an extra password protection to sensitive apps , this applock's password is different from your phone unlock password therefore you can safely lend out your phone / lock your private apps by using fingerprint pattern or pin and keep your secret safe from snoopers | personalize your unlocking app lock themes and make unlocking experience unique and interesting ; brand new app lock's themes updated : fingerprint unlocking is technologically supported specific devices and user friendly super fast energy efficient... Télécharger
user friendly super fast energy efficient and tiny virus cleaner only takes less than 10 sec to examine your entire phone with one tapvirus cleaner is powered by mcafee the powerful anti virus engine in the world protecting your phone from any of extortion virus malware trojans [...] we have official partnership with mcafee that is a part of intel security so hi security is able to offer the world class antivirus protection service globally , scheduled virus scan automatically scan your phone daily weekly or monthly / deep scan scanning and examining filesscanning both internal device storage and sd cards | remove viruses and threats from your mobile phone ; memory junk clean memory cleanscan and clean phone memory junk : optimize phone speed by releasing more phone memoriessafe browsing a real time online protectionblock malicious urls and protect yourself against phishing websites with instant warning notifications [...] app lock smart app lock with stylish lock themeswith it you can add an extra password protection to sensitive apps , this applock's password is different from your phone unlock password therefore you can safely lend out your phone / lock your private apps by using fingerprint pattern or pin and keep your secret safe from snoopers | personalize your unlocking app lock themes and make unlocking experience unique and interesting ; brand new app lock's themes updated : fingerprint unlocking is technologically supported specific devices and user friendly super fast energy efficient... Télécharger

Being imperceptible in the background the option of controlled folders of reaconverter allows the user to change the size of the images cut them adjust the brightness and colors add watermarks or edit images of more than 200 compatible formats that may have gone to the specified source folderreaconverter is a powerful batch image converter that allows you to convert several images from a large number of different formats in a single operation [...] the batch image converter supports a huge number of different formats so you can use it to open and convert images of any format you can find including rare and obsolete formats , in total 235 input image formats and 59 output formats are supported / supported formats include all standard and advanced formats raw formats used by digital photo professionals microsoft office documents as well as cad formats including dwg dxf dgn and many more | in addition to the standard conversion features of batch images you can also edit multiple images at once as well as resize reflect apply filters or watermarks and much more ; if you are looking for a sophisticated batch image converter reaconverter is the perfect solution : the new update of reaconverter 7 allows creative users to do what they should do: create without wasting time in routine operationsthe function is called watched folders and is used to identify new or modified files in image folders performing predetermined actions with them instantly [...] you can being imperceptible in the background the... Télécharger

Being imperceptible in the background the option of controlled folders of reaconverter allows the user to change the size of the images cut them adjust the brightness and colors add watermarks or edit images of more than 200 compatible formats that may have gone to the specified source folderreaconverter is a powerful batch image converter that allows you to convert several images from a large number of different formats in a single operation [...] the batch image converter supports a huge number of different formats so you can use it to open and convert images of any format you can find including rare and obsolete formats , in total 235 input image formats and 59 output formats are supported / supported formats include all standard and advanced formats raw formats used by digital photo professionals microsoft office documents as well as cad formats including dwg dxf dgn and many more | in addition to the standard conversion features of batch images you can also edit multiple images at once as well as resize reflect apply filters or watermarks and much more ; if you are looking for a sophisticated batch image converter reaconverter is the perfect solution : the new update of reaconverter 7 allows creative users to do what they should do: create without wasting time in routine operationsthe function is called watched folders and is used to identify new or modified files in image folders performing predetermined actions with them instantly [...] you can being imperceptible in the background the... Télécharger

The user interface is quite simple and you can drag and drop your flac files onto the program then the conversion would start instantly flac to mp3 mac will convert all your flac music at onceflac to mp3 mac is a free mac os application which converts flac to mp3 wma m4a aac ogg and wav audio formats [...] besides flac format the app could also convert other media formats to mp3 including video and audio media formats , the app also transfers the metadata and tags in flac into mp3 files so you could keep all tag information during the conversion / features: easy to use simply dropping flac songs onto the program would start the converting immediately | 6 output audio formats supports 6 most popular audio formats in the world: mp3 aac m4a ogg wav and wma ; convert other audio formats the application could also convert media files other audio formats as input to mp3 like wav wma and aac etc : audio extracting flac to mp3 mac can extract audio from all popular video formats like mp4 mov avi mpg wmv m4p no drm etcconvert in bulk drag & drop all your flac files to convert them at once [...] , the user interface is quite simple and you can... Télécharger
The user interface is quite simple and you can drag and drop your flac files onto the program then the conversion would start instantly flac to mp3 mac will convert all your flac music at onceflac to mp3 mac is a free mac os application which converts flac to mp3 wma m4a aac ogg and wav audio formats [...] besides flac format the app could also convert other media formats to mp3 including video and audio media formats , the app also transfers the metadata and tags in flac into mp3 files so you could keep all tag information during the conversion / features: easy to use simply dropping flac songs onto the program would start the converting immediately | 6 output audio formats supports 6 most popular audio formats in the world: mp3 aac m4a ogg wav and wma ; convert other audio formats the application could also convert media files other audio formats as input to mp3 like wav wma and aac etc : audio extracting flac to mp3 mac can extract audio from all popular video formats like mp4 mov avi mpg wmv m4p no drm etcconvert in bulk drag & drop all your flac files to convert them at once [...] , the user interface is quite simple and you can... Télécharger

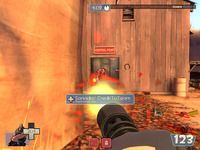
Ce fps multijoueur va vous engager dans des batailles tactiques où il faudra user des capacités inhérentes à votre classe tank ingénieurteam fortress 2 est un jeu gratuit qui a en quelque sorte relancé l'intérêt des fps f2p sur steam [...] pour espérer parvenir à la victoire , pas facile facile heureusement que vous améliorez vos stats au fil de la partie! un jeu incontournable qui regorge en plus de goodies / ce fps multijoueur va vous engager dans des... Télécharger

Ce fps multijoueur va vous engager dans des batailles tactiques où il faudra user des capacités inhérentes à votre classe tank ingénieurteam fortress 2 est un jeu gratuit qui a en quelque sorte relancé l'intérêt des fps f2p sur steam [...] pour espérer parvenir à la victoire , pas facile facile heureusement que vous améliorez vos stats au fil de la partie! un jeu incontournable qui regorge en plus de goodies / ce fps multijoueur va vous engager dans des... Télécharger
Clean junk to create a faster lighter and smoother user experiencea world class free antivirus and mobile security solution for android phones [...] the best antivirus protection no , 1 antivirus engine inside hi security is powered by mcafee the best antivirus engine in the world protecting your phone from any of extortion virus malware adware or trojans / we have official partnership with mcafee that is a part of intel security so hi security is able to offer the best antivirus protection service globally | applock privacy protectionwith hi security you can add an extra password protection to sensitive apps such as facebook message whatsapp tinder snapchat gallery and video ; this password is different from your phones unlock password therefore you can safely lend out your phone : protecting your privacy with pin pattern or fingerprintjunk clean phone memory releases intelligently analysis and remove junk files to free up more space and improve the performance of your device such as residual files cache temp files [...] now you can take more pictures and install apps , wifi security wi fi examination wi fi optimisation and wifi boosterhi security protects your online security to avoid insecure public wifi or phishing hotspot by detecting dns hijacking arp spoofing and ssl hijacking / boost wifi and enhance wifi signal strength for faster internet speed | intelligently manage your wifi ; no more wifi safety concerns : clean junk to create a faster lighter and... Télécharger
Clean junk to create a faster lighter and smoother user experiencea world class free antivirus and mobile security solution for android phones [...] the best antivirus protection no , 1 antivirus engine inside hi security is powered by mcafee the best antivirus engine in the world protecting your phone from any of extortion virus malware adware or trojans / we have official partnership with mcafee that is a part of intel security so hi security is able to offer the best antivirus protection service globally | applock privacy protectionwith hi security you can add an extra password protection to sensitive apps such as facebook message whatsapp tinder snapchat gallery and video ; this password is different from your phones unlock password therefore you can safely lend out your phone : protecting your privacy with pin pattern or fingerprintjunk clean phone memory releases intelligently analysis and remove junk files to free up more space and improve the performance of your device such as residual files cache temp files [...] now you can take more pictures and install apps , wifi security wi fi examination wi fi optimisation and wifi boosterhi security protects your online security to avoid insecure public wifi or phishing hotspot by detecting dns hijacking arp spoofing and ssl hijacking / boost wifi and enhance wifi signal strength for faster internet speed | intelligently manage your wifi ; no more wifi safety concerns : clean junk to create a faster lighter and... Télécharger

Mp4 converter key features: convert avi to mp4 video format; convert mpeg to mp4 video format; convert wmv to mp4 video format; convert asf asx to mp4 video format; convert quick time to mp4 video format; easy to use and user friendly interface; convert dvd vob files to mp4 video format directly; mp4 converter supports video formats: *mp4 converter for windows is aa easy to use video to mp4 converter very useful for converting video avi mpeg wmv asf asx to mp4 without any quality loss [...] and convert dvd vob files to mp4 video format for playing on iphone ipad ipod touch samsung smart tv android tablets amazon kindle smartphones portable media players etc , mp4 converter is a video to device converter support convert popular video formats: * / avi * | wmv * ; asf * : asx *mpg * [...] m1v * , m2v * / m2p * | vob etc ; to mp4 video format : [...] , mp4 converter key features: convert avi to mp4... Télécharger

Mp4 converter key features: convert avi to mp4 video format; convert mpeg to mp4 video format; convert wmv to mp4 video format; convert asf asx to mp4 video format; convert quick time to mp4 video format; easy to use and user friendly interface; convert dvd vob files to mp4 video format directly; mp4 converter supports video formats: *mp4 converter for windows is aa easy to use video to mp4 converter very useful for converting video avi mpeg wmv asf asx to mp4 without any quality loss [...] and convert dvd vob files to mp4 video format for playing on iphone ipad ipod touch samsung smart tv android tablets amazon kindle smartphones portable media players etc , mp4 converter is a video to device converter support convert popular video formats: * / avi * | wmv * ; asf * : asx *mpg * [...] m1v * , m2v * / m2p * | vob etc ; to mp4 video format : [...] , mp4 converter key features: convert avi to mp4... Télécharger

Our software has one of the simplest and most user friendly interface for you to carry out your email marketing business without any difficultyyou are someone who needs to communicate with a large list of customers or subscribers [...] emailsaler can simplify your e mail marketing campaign it allows you to easily design rich html emails send a personalized copy of your e mail to each address in your mailing list and each recipient sees only its own e mail adress , easy to use interface at emailsaler we understand that it is not necessary to acquire a degree in computer science before entering into email marketing / that's why we keep things very simple and simple | multiple task management emailsaler allows you to create multiple sending jobs simultaneously ; you can edit copy execute or stop a task at any time you want : it also allows you to monitor the progress of sending each task you can give your full attention to the task in front of youcustomizing email using e mail merge the rate of reading and opening e mails can be maximized if your customer sees his or her name or name in the subject line [...] the overall impact of your email can be even greater if you use the mail merge feature of our mass mailing software , you will never return anonymous mailing lists you will use your stored data to compose a very attractive and personalized email / automatic cancellation and rebound management the emailsaler bounce handler can automatically unsubscribe or delete our software has one of the simplest and most... Télécharger

Our software has one of the simplest and most user friendly interface for you to carry out your email marketing business without any difficultyyou are someone who needs to communicate with a large list of customers or subscribers [...] emailsaler can simplify your e mail marketing campaign it allows you to easily design rich html emails send a personalized copy of your e mail to each address in your mailing list and each recipient sees only its own e mail adress , easy to use interface at emailsaler we understand that it is not necessary to acquire a degree in computer science before entering into email marketing / that's why we keep things very simple and simple | multiple task management emailsaler allows you to create multiple sending jobs simultaneously ; you can edit copy execute or stop a task at any time you want : it also allows you to monitor the progress of sending each task you can give your full attention to the task in front of youcustomizing email using e mail merge the rate of reading and opening e mails can be maximized if your customer sees his or her name or name in the subject line [...] the overall impact of your email can be even greater if you use the mail merge feature of our mass mailing software , you will never return anonymous mailing lists you will use your stored data to compose a very attractive and personalized email / automatic cancellation and rebound management the emailsaler bounce handler can automatically unsubscribe or delete our software has one of the simplest and most... Télécharger

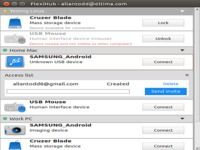
Your shared device can be accessed and used by any flexihub user you inviteflexihub is a software that enables you to access and manage usb devices remotely over network [...] thus for example you can send documents for a printout to your office printer while you are working from home or access the contents of a usb dongle attached to your colleague’s pc as long as you are in the network , flexihub works as a control panel for all shared usb devices in the network forming a hardware cloud accessible by network users / there is absolutely no difference whether the device you access is attached to your computer or another computer somewhere else | using the app is really easy you first have to download and install it ; flexihub consists of server and client parts: the former goes to a computer whose usb ports are to be shared and the latter – to computers that need access to these ports : the application will list all computers in the network as nodes and you will see usb devices attached to themthe app also displays information about devices’ types so it is easier for you to find the device you need to connect to [...] sharing usb devices with the help of flexihub is safe and secure thanks to 256 bit ssl encryption , no unauthorized party can access your data / data traffic is reduced by flexihub via data compression | information for developers: flexihub can be integrated into other software solutions and distributed as part of them ; you can sign up your shared device can be accessed and used by... Télécharger

Your shared device can be accessed and used by any flexihub user you inviteflexihub is a software that enables you to access and manage usb devices remotely over network [...] thus for example you can send documents for a printout to your office printer while you are working from home or access the contents of a usb dongle attached to your colleague’s pc as long as you are in the network , flexihub works as a control panel for all shared usb devices in the network forming a hardware cloud accessible by network users / there is absolutely no difference whether the device you access is attached to your computer or another computer somewhere else | using the app is really easy you first have to download and install it ; flexihub consists of server and client parts: the former goes to a computer whose usb ports are to be shared and the latter – to computers that need access to these ports : the application will list all computers in the network as nodes and you will see usb devices attached to themthe app also displays information about devices’ types so it is easier for you to find the device you need to connect to [...] sharing usb devices with the help of flexihub is safe and secure thanks to 256 bit ssl encryption , no unauthorized party can access your data / data traffic is reduced by flexihub via data compression | information for developers: flexihub can be integrated into other software solutions and distributed as part of them ; you can sign up your shared device can be accessed and used by... Télécharger
Ao oni 2 ou blue demon 2 ou 青鬼2 en japonais va vous mettre dans une situation délicate: seul enfermé dans une école vous allez devoir rivaliser d'ingéniosité pour résoudre des énigmes mais aussi user de votre dextérité pour échapper aux démons bleus qui vous coursent dans les couloirs et les salles d'une école labyrinthiqueblue demon est un jeu pc créé sous rpg maker qui a connu un petit succés lors de sa sortie à tel point qu'un film inspiré par l'intrigue a vu le jour [...] la sortie de la suite du premier film a encouragé les développeurs à sortir un nouveau jeu cette fois sur mobiles dont voici la version android , le principe est simple: perdu dans l'école dans laquelle vous êtes prisonnier vous devez semer les démons bleus qui essaient de vous torturer et trouver un moyen de sortir en résolvant des énigmes dignes des meilleurs escape game / le jeu est en japonais mais peut être arriverez vous à comprendre l'intrigue et à avancer douloureusement dans le manoir avec vos amis | ao oni 2 blue demon 2 n'est pas conseillé aux personnes sensibles ; l'apk du jeu est téléchargeable ci dessous : ao oni 2 ou blue demon 2 ou 青鬼2 en... Télécharger
Ao oni 2 ou blue demon 2 ou 青鬼2 en japonais va vous mettre dans une situation délicate: seul enfermé dans une école vous allez devoir rivaliser d'ingéniosité pour résoudre des énigmes mais aussi user de votre dextérité pour échapper aux démons bleus qui vous coursent dans les couloirs et les salles d'une école labyrinthiqueblue demon est un jeu pc créé sous rpg maker qui a connu un petit succés lors de sa sortie à tel point qu'un film inspiré par l'intrigue a vu le jour [...] la sortie de la suite du premier film a encouragé les développeurs à sortir un nouveau jeu cette fois sur mobiles dont voici la version android , le principe est simple: perdu dans l'école dans laquelle vous êtes prisonnier vous devez semer les démons bleus qui essaient de vous torturer et trouver un moyen de sortir en résolvant des énigmes dignes des meilleurs escape game / le jeu est en japonais mais peut être arriverez vous à comprendre l'intrigue et à avancer douloureusement dans le manoir avec vos amis | ao oni 2 blue demon 2 n'est pas conseillé aux personnes sensibles ; l'apk du jeu est téléchargeable ci dessous : ao oni 2 ou blue demon 2 ou 青鬼2 en... Télécharger