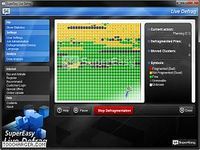
Having a cleaned up hard disk drive means for example that applications run faster and the copying of files as well as the opening of photos is acceleratedthe most important features: fully automatic background monitoring ssd hard disk protection weekly statistics timer raid hard disk support removal of disk space gaps support for external usb hard disks accelerated copying and opening of photos [...] supereasy live defrag free cleans up fragmented hard disks automatically and intelligently pauses as soon as other applications need system resources , supereasy live defrag free is easy to use without complex settings / it starts its job automatically if desired and relieves you of all the work | you can customize the defragmentation by using a timer or setting a defragmentation task ; having a cleaned up hard disk drive means for... Télécharger

Having a cleaned up hard disk drive means for example that applications run faster and the copying of files as well as the opening of photos is acceleratedthe most important features: fully automatic background monitoring ssd hard disk protection weekly statistics timer raid hard disk support removal of disk space gaps support for external usb hard disks accelerated copying and opening of photos [...] supereasy live defrag free cleans up fragmented hard disks automatically and intelligently pauses as soon as other applications need system resources , supereasy live defrag free is easy to use without complex settings / it starts its job automatically if desired and relieves you of all the work | you can customize the defragmentation by using a timer or setting a defragmentation task ; having a cleaned up hard disk drive means for... Télécharger

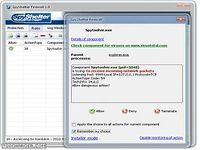
More sophisticated programs can capture everything a user sees on his screen when performing a screen capture: just the mere opening of a file can allow an information thief to steal your dataspyshelter anti keylogger can protect you against attacks that happen even when you do ordinary computer tasks like: typing into your computer getting screenshots opening files and visiting sites [...] you need the spyshelter firewall ! the internet is now a vital part of our personal and business lives , with increasing use of online systems cybercrime also has grown exponentially / information stealing software are produced regularly and are used by thieves to steal personal and business information | one of the most effective ways of stealing information is through a program that can easily be made to capture keystrokes ; this program captures everything that a user is doing keystrokes mouseclicks files opened and closed sites visited and network traffic : these sophisticated and dangerous programs are called keylogging programs eg [...] keyloggers key recorder keytrappers key capture programs etc , and they are developed continuously all over the world / the spyshelter monitors vulnerable and weak spots in your computer system to ensure that even the most advanced keyloggers are shut down even before these can launch a single dangerous attack against your computer | two way internet firewall: locks out hackers blocks intrusions provides incoming/outgoing network more sophisticated programs can capture... Télécharger

More sophisticated programs can capture everything a user sees on his screen when performing a screen capture: just the mere opening of a file can allow an information thief to steal your dataspyshelter anti keylogger can protect you against attacks that happen even when you do ordinary computer tasks like: typing into your computer getting screenshots opening files and visiting sites [...] you need the spyshelter firewall ! the internet is now a vital part of our personal and business lives , with increasing use of online systems cybercrime also has grown exponentially / information stealing software are produced regularly and are used by thieves to steal personal and business information | one of the most effective ways of stealing information is through a program that can easily be made to capture keystrokes ; this program captures everything that a user is doing keystrokes mouseclicks files opened and closed sites visited and network traffic : these sophisticated and dangerous programs are called keylogging programs eg [...] keyloggers key recorder keytrappers key capture programs etc , and they are developed continuously all over the world / the spyshelter monitors vulnerable and weak spots in your computer system to ensure that even the most advanced keyloggers are shut down even before these can launch a single dangerous attack against your computer | two way internet firewall: locks out hackers blocks intrusions provides incoming/outgoing network more sophisticated programs can capture... Télécharger